About Arctic Wolf
Security Operations
Concierge Delivery
Resources
Get in Touch
Primesys are proudly an
Arctic Wolf Partner
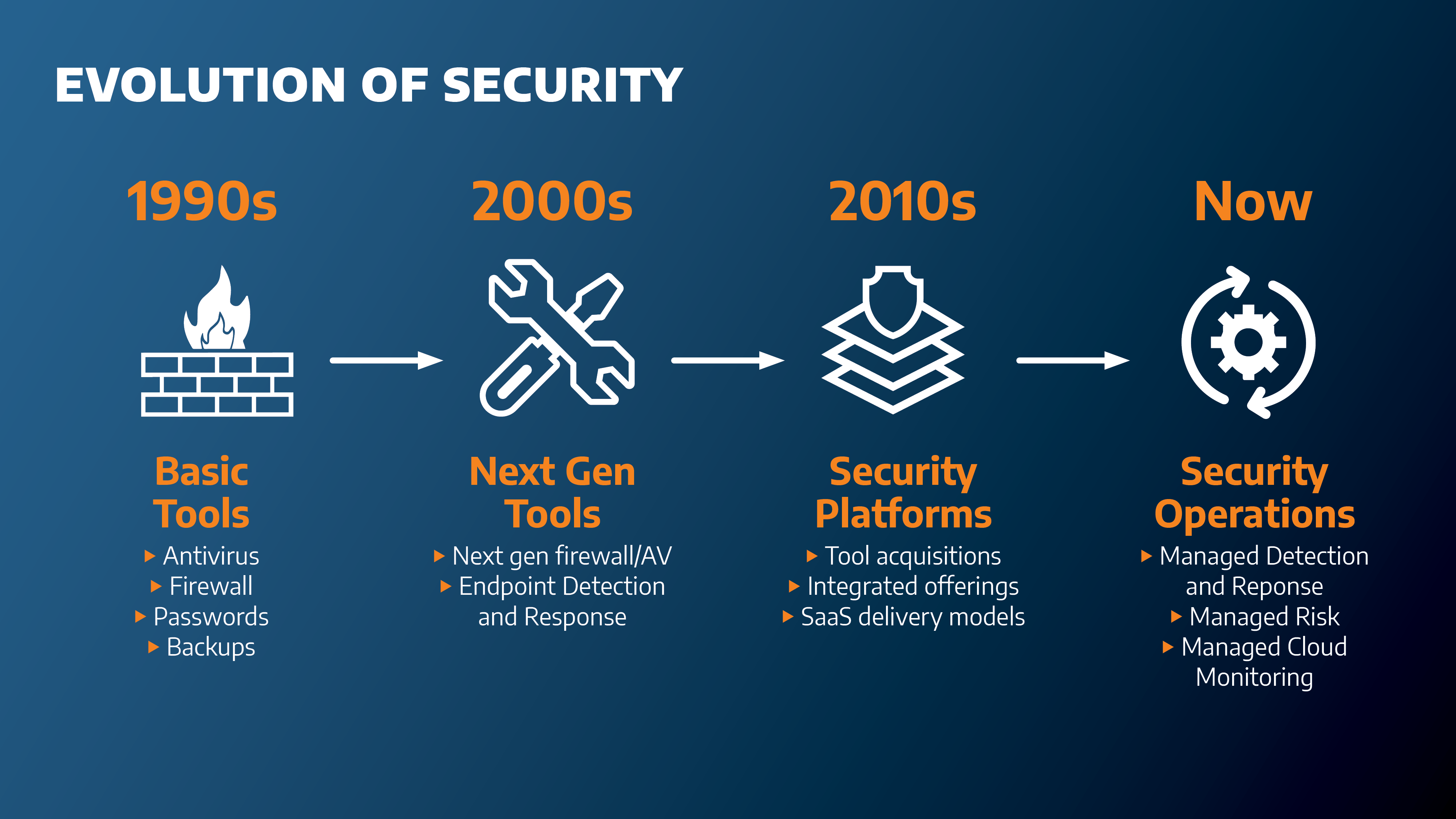
About Arctic Wolf
Using the cloud-native Arctic Wolf® Platform, we help organisations end cyber risk by providing security operations as a concierge service. Arctic Wolf solutions include Arctic Wolf® Managed Detection and Response (MDR), Managed Risk, Managed Security Awareness, and Incident Response; each delivered by a Concierge Delivery Model.
Highly-trained security experts work as an extension of internal teams to provide 24×7 monitoring, detection and response, as well as ongoing risk management to proactively protect organisations while continually strengthening their security posture.
PrimeSys are proud to be an Arctic Wolf Partner.
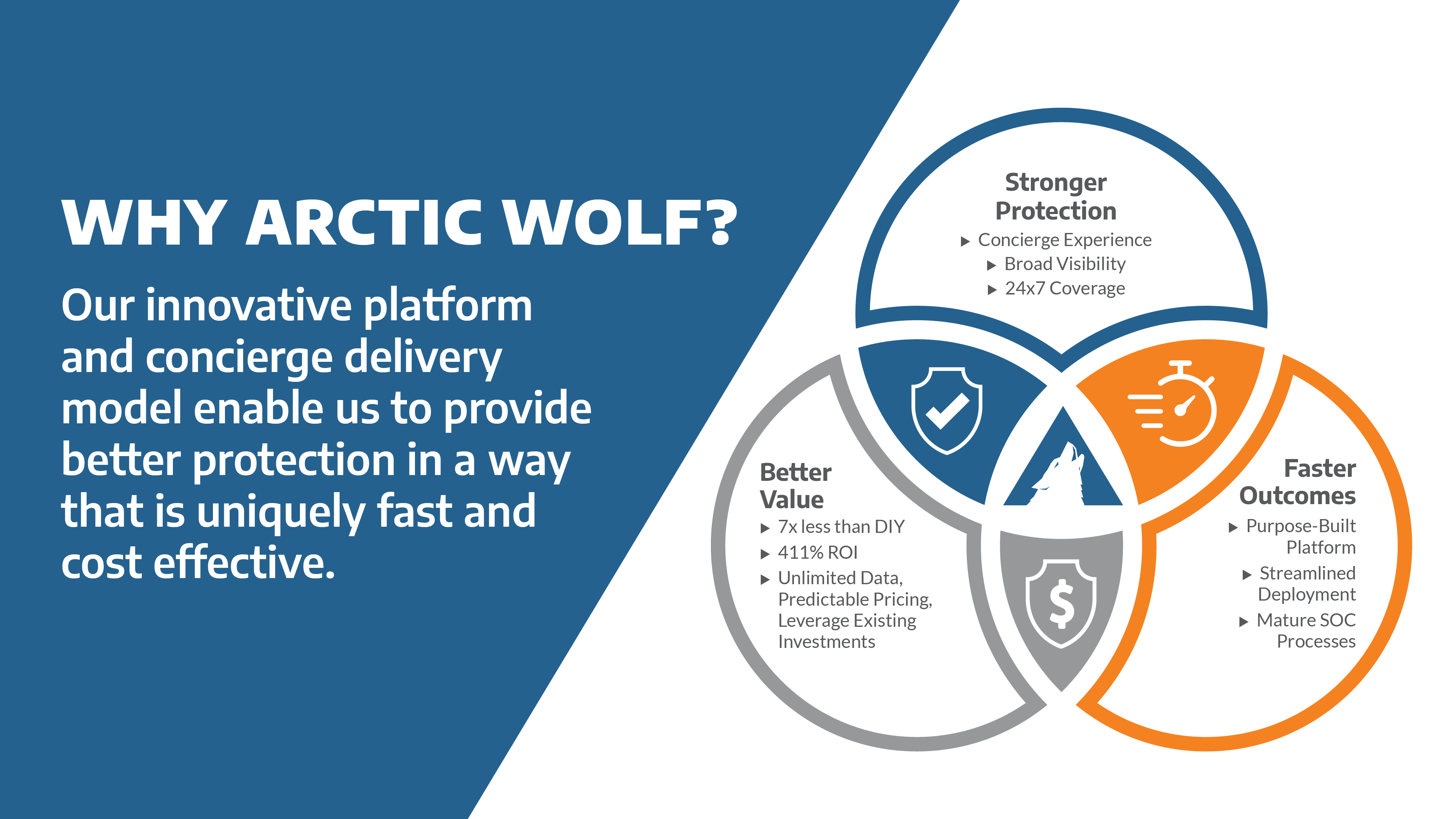
Security Operations Platform
Spanning thousands of installations, the Arctic Wolf Platform processes over 5 trillion security events weekly. Built on an open XDR architecture, the platform collects and enriches endpoint, network, and cloud telemetry, and then analyses it within multiple detection engines.
Machine learning and custom detection rules then deliver personalised protection for your organisation. While other products have limited visibility, the vendor-neutral Arctic Wolf Platform enables broad visibility and works seamlessly with existing technology stacks, making it easy to adopt while eliminating blind spots and vendor lock-in.
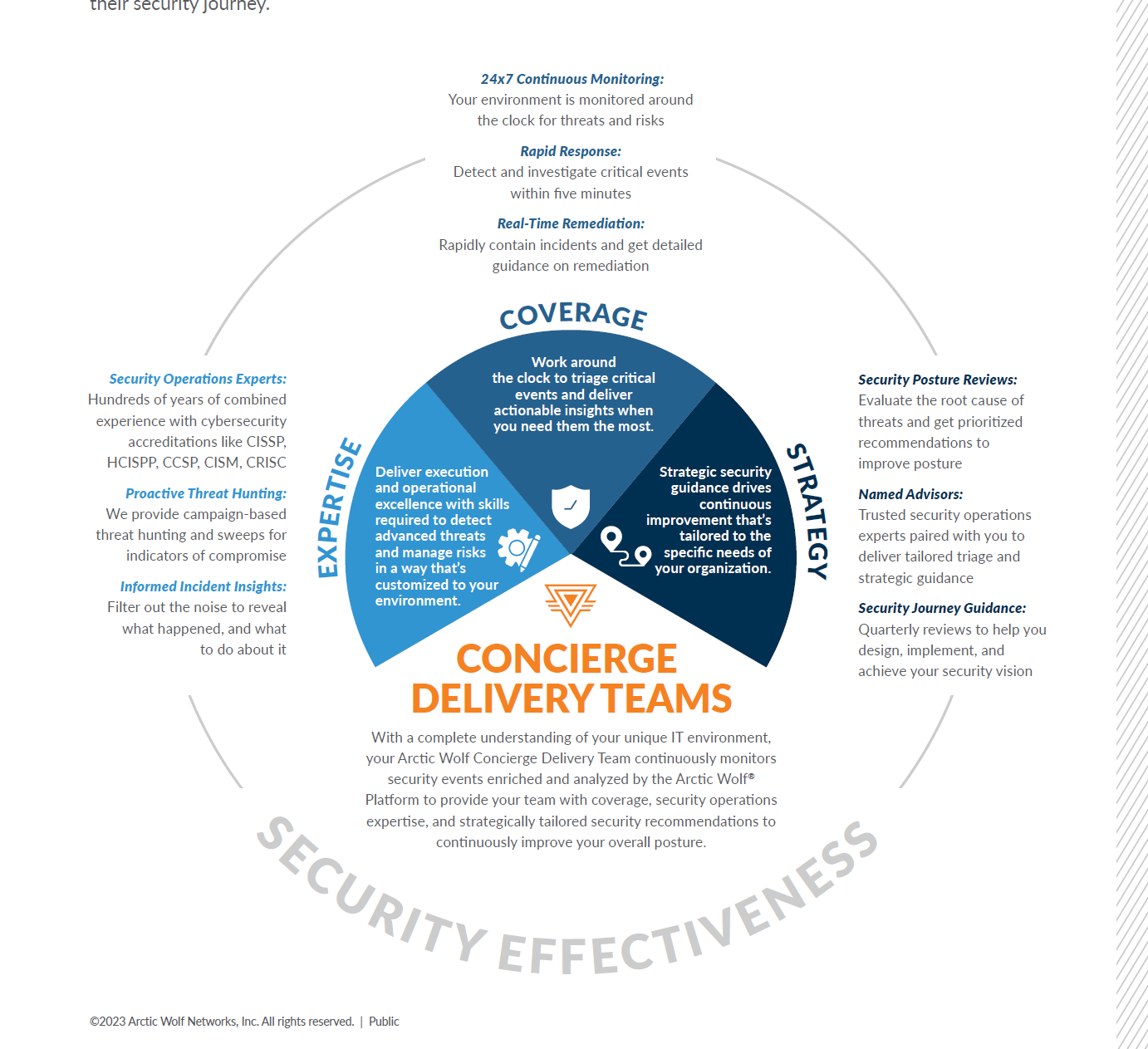
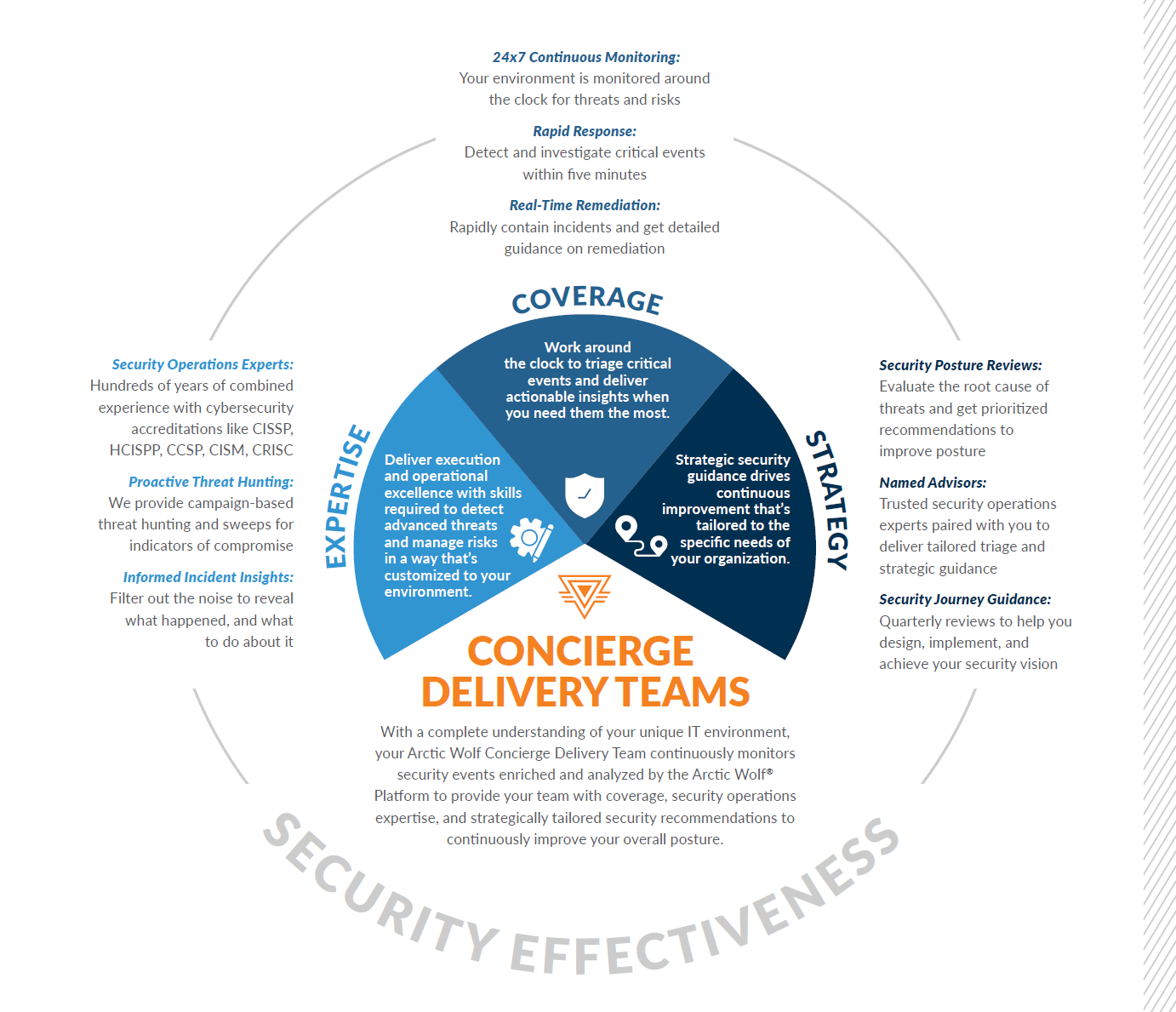
Concierge Delivery Model
The modern threat landscape is evolving, and attack surfaces are growing. At the same time, the security skills gap means it is more challenging than ever to find, train, and retain enough security experts to staff and maintain and effective in-house SOC.
The Arctic Wolf Concierge Delivery Model provides you with holistic visibility into your entire environment while reducing alert fatigue and driving continuous improvement tailored to the specific needs of your organisation.
If you’re looking to partner with an Arctic Wolf reseller, please get in touch.
Resources
Download the Arctic Wolf Labs Report – 2024 Predictions here…
Additional Resources
Request Information
Request a Quote
Request Information
Please use the form to request information about our Arctic Wolf services.
Need Help?
CALL
01452 924202
info@primesys.co.uk
Request a Quote
Please use the form to request a quote for our Arctic Wolf services.
Need Help?
CALL
01452 924202
info@primesys.co.uk
Connected Services
Security for Networks,
Devices & Users.